When the Assembly Line Lies Silent: Lessons from the JLR Cyberattack
30th Sep 2025
Speak to an expert
30th Sep 2025
Earlier this month, Jaguar Land Rover (JLR) confirmed a cyberattack had forced it to shut down systems and suspend production. The impact has been severe, with JLR’s UK factories standing still for weeks. The fallout has hit suppliers, staff, and customers. Despite production gradually returning online, the UK government has pledged a £1.5 billion loan guarantee to prevent long-term damage to the automotive supply chain. The situation highlights how digital risk can quickly become an industry-wide crisis.
This article explores the known facts, outlines the lessons, and sets out practical steps organisations can take. Most importantly, it considers how resilience can be built to withstand disruption and protect business continuity.
According to JLR, the incident began in late August 2025. Systems were taken offline to contain the threat, which brought production lines to a halt. While the company has said that “some data” was affected, the full scale of the breach remains unclear.
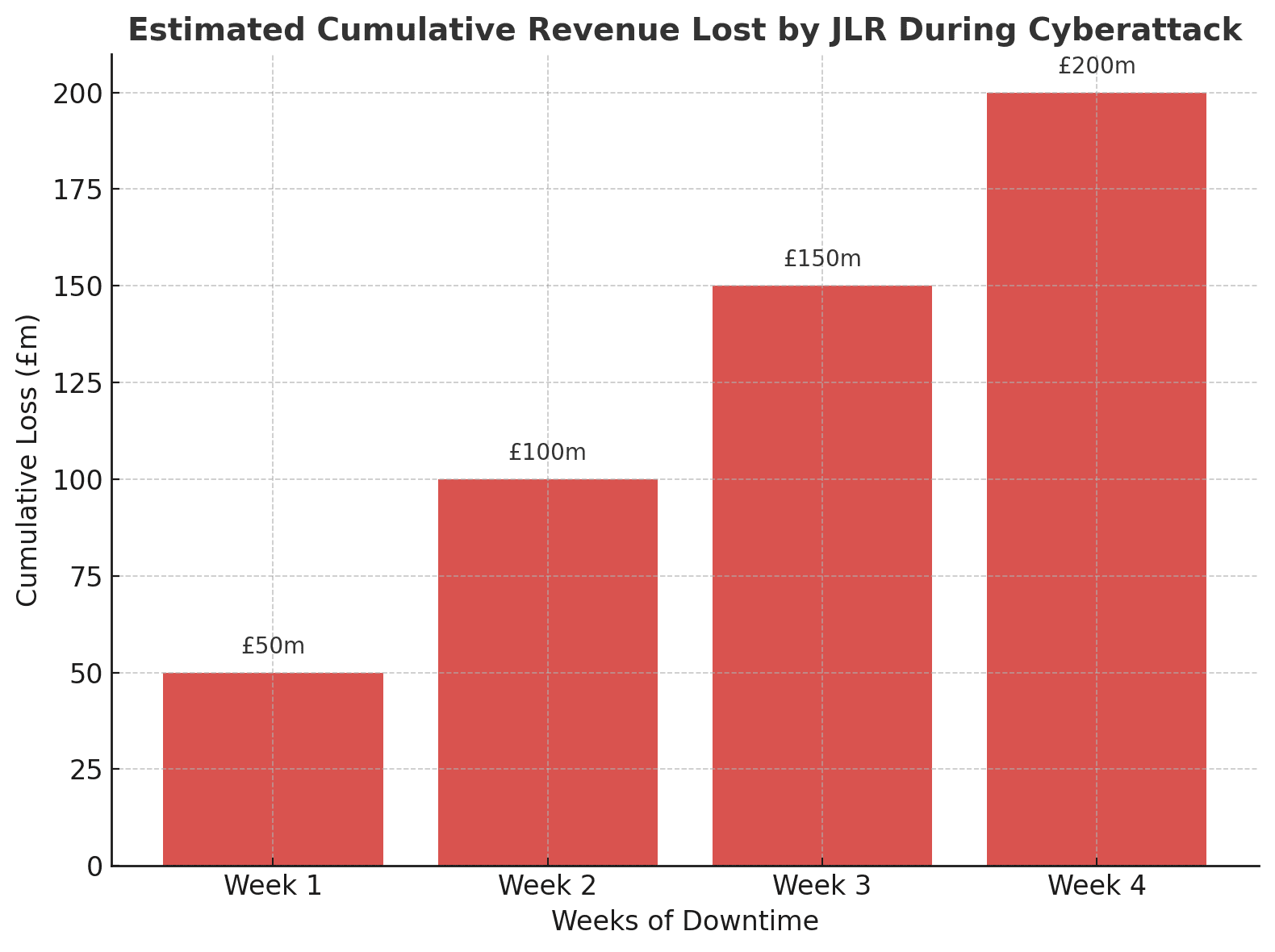
The financial damage is already significant. Analysts estimate losses of around £50 million each week production was halted. To make matters worse, JLR had not finalised its cyber insurance, leaving it exposed to the full cost of disruption. Suppliers have also been put under strain, with many dependent on just-in-time deliveries and thin margins.
Although investigations are ongoing, early reports suggest attackers may have exploited weaknesses in vendor software. This pattern is familiar, with adversaries often targeting third-party systems as an entry point. Other recent high-profile third-party system breaches have occurred in the retail sector, with Marks & Spencer, Harrods and the Co-op being affected. Several European airports have also been impacted following a booking system breach that resulted in widespread flight delays and cancellations.
At the time this article was published, JLR has restarted portions of its IT systems, including those supporting payments, parts logistics, and vehicle registration. Although full production remains suspended, this step is crucial to restoring cash flow and supporting the aftermarket parts pipeline.
Despite this progress, JLR’s factories across its UK, Slovakia, India and Brazil plants will remain offline at least until 1 October 2025, after revised assessments extended the shutdown. The scale of the interruption has forced JLR to prioritise stabilising operations before resuming full output.
Losses are mounting and some forecasts suggest that, if delays stretch into November, the total cost could surpass £3.5 billion.
UK vehicle production dropped 18.2% in August 2025, exacerbated by JLR’s forced pause. As a result, customers will be impacted by extended vehicle delivery lead times.
JLR has restarted payments for parts already delivered and ramped up IT capacity to clear invoices. However, many suppliers are under extreme pressure: some have laid off workers, and others are warning of closures unless support is forthcoming.
In a substantial intervention, the UK government has pledged a £1.5 billion loan guarantee to back JLR’s recovery and underwriting of supplier exposures. The guarantee is designed to help liquidity among suppliers and maintain continuity across the automotive ecosystem.
However, the guarantee has sparked debate over “moral hazard” – whether state intervention might reduce incentives for organisations to invest in cyber resilience or maintain cyber insurance.
Meanwhile, ministers remain under pressure to support suppliers directly, whether via government purchases of parts, low-interest backed loans, or other liquidity measures.
Cyber insurance is not a substitute for strong controls. Yet without cover, recovery costs can spiral. JLR’s timing misstep is a reminder to all organisations: insurance must be locked down and underpinned by robust cyber maturity.
Insight: Review your current cover and ensure it aligns with the risks your organisation faces.
When one node in the chain falters, the effects cascade. JLR’s suppliers are facing lost revenue, paused operations and staff layoffs. Organisations must treat supply chain cyber risk as a board-level issue.
Insight: Consider supply chain mapping and assessing vendor dependencies to reduce single points of failure.
In modern manufacturing, IT systems and operational technology are tightly integrated. A breach in one can disable the other. Effective segmentation and holistic monitoring are therefore, critical.
Insight: Review whether your IT and OT networks are appropriately segmented and monitored for suspicious activity.
Third-party applications are often trusted implicitly, yet they can harbour unpatched vulnerabilities. Without proper oversight, they become attackers’ preferred route in.
Insight: Ensure your patching schedules, change controls and vendor assurance processes are robust and regularly penetration tested.
JLR acted quickly to contain the breach. However, extended downtime shows the challenge of recovery without fully rehearsed playbooks. Speed, clarity, and co-ordination determine whether an organisation survives an incident.
Insight: Test your incident response plan through exercises and simulations to build confidence in your ability to recover under pressure.
With a £1.5 billion government guarantee in play, the JLR case now straddles public policy, industrial strategy and corporate risk. The move changes the risk calculus: supporters see it as a necessary lifeline; critics warn of precedent and dependency.
Insight: Organisations with large industrial or supply chain footprints should include political, regulatory and reputation risk in their cyber resilience modelling. The possibility of state intervention, reputational scrutiny or regulatory investigations is real – plan for it.
The JLR incident demonstrates that preparedness is the difference between resilience and disruption. Organisations that act now can reduce exposure, accelerate recovery and maintain trust. Building strength is not about a single control; it is about a balanced programme that addresses prevention, detection, response and recovery together.
Here are five practical areas to focus on, with examples of how they can be strengthened:
Carrying out an independent review of your cyber posture can identify blind spots before attackers do. These reviews highlight where investment will have the greatest impact.
How we can help: Assure Technical delivers tailored cyber resilience assessments that benchmark maturity, prioritise risks and set out clear roadmaps for improvement.
No organisation operates in isolation. Supplier compromise can have the same effect as a direct attack. Building resilience means knowing where the weak links are and working with partners to improve them.
How we can help: We conduct supply chain security audits and vendor risk assessments to uncover dependencies and reduce systemic vulnerabilities.
Insurance is not a replacement for security, but it plays a vital role in financial resilience. However, cover is increasingly linked to evidence of good practice. Aligning insurance and security maturity avoids unexpected gaps.
How we can help: Our insurance readiness reviews help organisations demonstrate robust controls, ensuring that coverage is both attainable and cost-effective.
Even the strongest defences cannot guarantee prevention. What matters next is the ability to detect quickly, contain effectively and recover with confidence. Incident response plans must be practical, rehearsed and supported by the right tools.
How we can help: Assure Technical provides incident response planning, tabletop exercises and managed detection & response services, ensuring teams know what to do when every minute counts.
Threats evolve daily. Controls that worked last year may not be effective tomorrow. Regular testing – from vulnerability scanning to red teaming – keeps defences sharp and builds confidence in resilience.
How we can help: We deliver continuous testing programmes that combine penetration testing, threat-led assurance and ongoing monitoring, helping organisations stay one step ahead.
Resilience is built in layers: strategy, governance, technology and people. Organisations that treat cyber security as an enabler – not just a compliance obligation – gain more than protection. They also benefit from stronger reputations, closer relationships with partners and a competitive edge in the marketplace.
Assure Technical works alongside organisations at every stage of this journey – from identifying risks to implementing and validating defences. Our role is to provide clarity, expertise and assurance, so that leaders can focus on growth with confidence.
The JLR cyberattack has shown how quickly disruption can escalate from an IT issue to a full-scale business crisis. The consequences extend far beyond lost production – they touch customers, suppliers, employees and reputations.
Yet there is a positive lesson here. Incidents like this highlight the value of building resilience early. By investing in preparedness, organisations not only reduce risk but also strengthen trust, ensure operational continuity and protect long-term growth.
Every organisation’s journey to resilience will look different. For some, the focus will be supply chain dependencies. For others, it may be insurance alignment or incident response rehearsals. What matters is that the journey begins before a crisis strikes.
At Assure Technical, we work with organisations to chart this path, combining independent insight with practical solutions. If you would like to explore how these lessons apply to your business, get in touch – our team of pragmatic, cybersecurity experts is always open to a conversation
Get in touch with our expert consultants for straight-talking, jargon-free technical security advice.












