Cyber Essentials Montpellier Update Explained
15th Mar 2023
Talk to our experts today
15th Mar 2023
On 24th April 2023 the Cyber Essentials Montpellier update was introduced. This blog provides information about the Cyber Essentials scheme and a useful summary about these changes.
According to the Cyber Security Breaches Survey 2022 reported that 39% of UK businesses identified a cyber-attack within a 12-month period. One in 5 companies reported that a cyber attack had a detrimental impact on their business.
It’s no surprise therefore, that 80% of businesses state that their board sees cyber security as a high priority. This is reflected in the growing number of supply chains are mandating Cyber Essentials certification.
Cyber Essentials is a UK Government approved certification that sets the baseline standard for organisations to protect themselves from the majority of cyber attacks. A growing number of organisations have gained this certification in order to bolster their cyber defences and reassure their stakeholders that they take cyber security seriously.
There are five key controls within the standard. These are:
Organisations are awarded Cyber Essentials certification when they are able to demonstrate that they comply with the requirements of standard. It involves completing a self assessment questionnaire and certification. Cyber Essentials Plus is awarded when organisations are then audited to prove their systems are working as they should. Certification is valid for 12 months, much like a MOT for your cyber security.
The cyber threat landscape constantly evolves, so it is paramount that the Cyber Essentials standard is regularly reviewed to ensure that it remains relevant and effective.
IASME, the sole Accreditation Body for Cyber Essentials, released the ‘Evendine’ question set in January 2022. This represented the biggest update to the standard since it’s launch.
On 24th April 2023 the ‘Montpellier’ question set was introduced. Any assessment accounts set up on or after this date will need to adhere to the new question set.
The Cyber Essentials Montpellier update builds upon the changes established by Evendine, improving its accessibility and introducing some new elements to the Cyber Essentials Plus audit. The changes may be less significant, but they represent a necessary evolution towards stronger cybersecurity practices.
Pete Lannon, Technical Director – Assure Technical
The definition as been updated as follows:
Software includes operating systems, commercial off-the-shelf applications, plugins, interpreters, scripts, libraries, network software and firewall and router firmware.
Organisations will be required to provide the make and model of firmware devices, which will enable Certification Bodies to determine if they are still receiving security updates.
The reason for this change is that firewall and router firmware acts as the operating system of these devices – keeping them up to date is extremely important from a security perspective.
Whilst asset management isn’t a specific Cyber Essentials control, establishing and maintaining authoritative and accurate asset information is recommended as a core security function.
By including this subject in the Cyber Essentials requirements, the importance of good asset management is being emphasised.
Comprehensive guidance for organisations on asset management can be found on the NCSC website.
The Cyber Essentials standard now provides further information and advice on the use of BYOD, please see the NCSC’s guidance.
The standard requires that all end user devices that your organisation owns and that are loaned to a third party must be included in the assessment scope. IASME has created the following table to provide clarity:
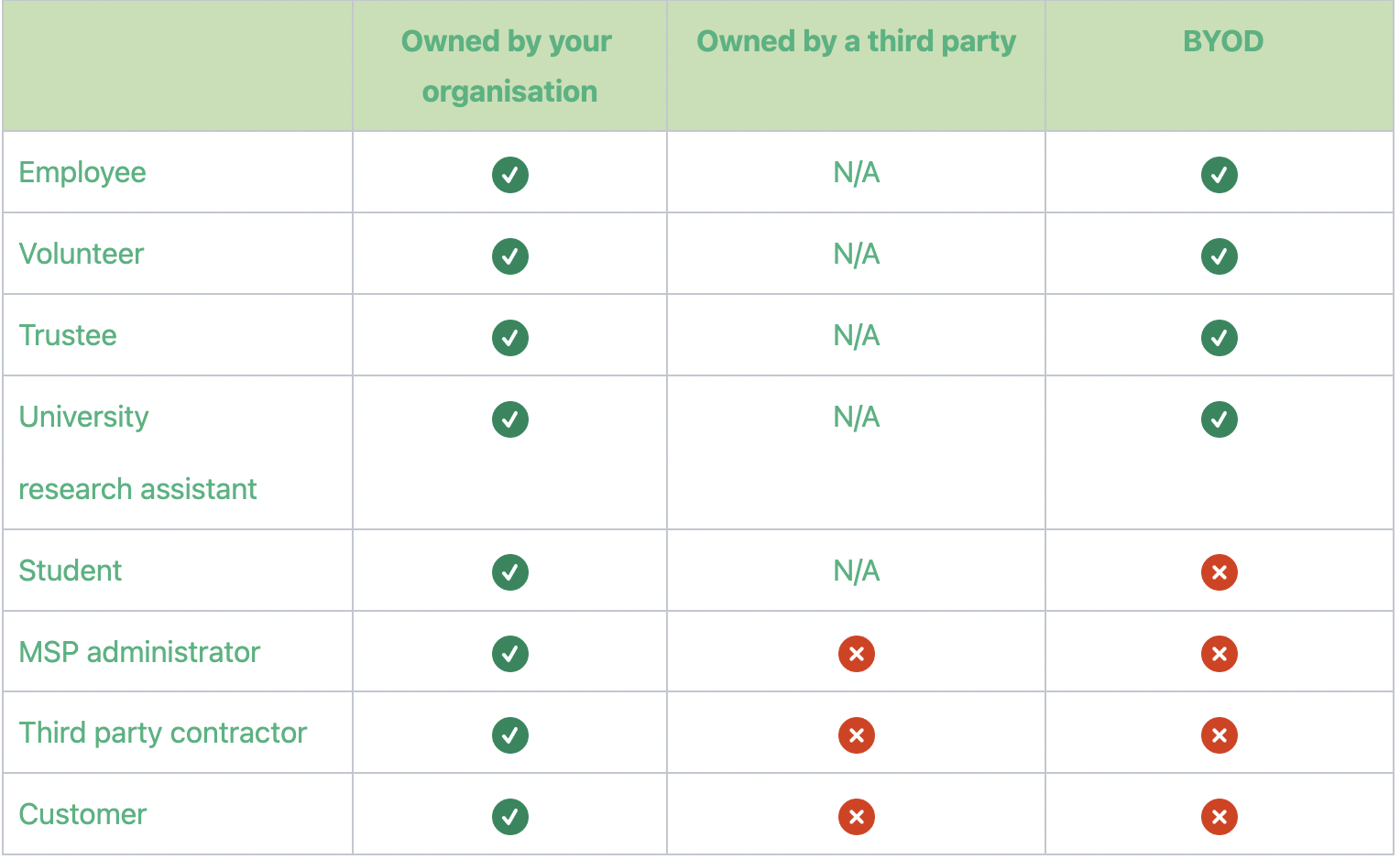
Sometimes, an applicant might be using a device where there are no options to change the configuration to meet the Cyber Essentials requirements e.g. locking the mobile devices after a defined number of failed sign-in attempts. In this instance, Cyber Essentials would require that the applicant goes with the minimum number sign-in attempts allowed by the device before locking.
Questions have been raised about the efficacy of some of the controls to defend against malware.
Cyber Essentials now requires a malware protection mechanism to be active and kept up to date according to vendor instructions on all devices in scope. ‘Sandboxing’ is no longer an option as an anti-malware control.
At least one of the following options must be used:
If you use anti-malware software to protect your device it must be configured to:
Only approved applications, restricted by code signing, are allowed to execute on devices. You must:
Network architecture is changing:
Zero trust architecture is an approach to system design where inherent trust in the network is removed, hence designed to cope with these changing conditions. They enable an improved user experience for remote access and data sharing.
The NCSC website contains more information about zero trust architecture.
One of the most significant changes to the new release is that Cyber Essentials Plus Assessors are required to carry out internal credentialed patch audits. This involved scanning a sample of internally hosted servers, in addition to user workstations. This is because, in recent breaches, unsupported server operating systems or out of date software on those servers has been the root cause of compromise.
There are changes to how a Cyber Essentials Plus Assessor carries out the malware protection tests.
The requirements document has been updated in line with plain English and accessibility guidelines.
For consistency, the scheme requirements are now in the same order as the Cyber Essentials self assessment questionnaire. This is; firewalls, secure configuration, security update management, user access controls, then malware protection.
There is no need for you to worry about the impact these changes will have on your forthcoming Cyber Essentials certification. As the most trusted Cyber Essentials Certification Body in the UK, our team of experienced assessors will pragmatic and jargon-free support to ensure that the process is as pain free as possible.
Get in touch with our expert consultants for straight-talking, jargon-free technical security advice.













